28 Additional Security Services in AWS
28.0.1 The Concept of Encryption
Encryption is a method of securing messages or data so that only authorised parties can access them. Unauthorised parties are therefore unlikely or unable to access the data. Imagine it as a key and door scenario: if you have the key, you can unlock the door; if you don’t, you cannot.
28.0.2 Encryption in AWS
At AWS, encryption comes in two variations: encryption at rest and encryption in transit.
- Encryption at Rest: This refers to data being secured while it is stored and not actively moving. For example, server-side encryption at rest is enabled on all DynamoDB table data, helping prevent unauthorised access. DynamoDB’s encryption at rest integrates with AWS Key Management Service (KMS) for managing the encryption key used to encrypt your tables. Without this key, you cannot access your data, so it is vital to keep it safe.
- Encryption in Transit: This means data is secured while it is moving between two points, such as between an AWS service and a client. For example, when connecting a Redshift instance to a SQL client, secure sockets layer (SSL) connections are used to encrypt data, and service certificates validate and authorise the client. This ensures data is protected while passing between Redshift and the client. Similar functionality exists in numerous other AWS services, such as SQS, S3, and RDS.
28.0.3 Amazon Inspector
Amazon Inspector helps improve the security and compliance of your AWS-deployed applications by running automated security assessments against your infrastructure. It checks for deviations from security best practices, exposure of EC2 instances, vulnerabilities, and more. The service consists of three parts:
- Network Configuration Reachability: Examines the network configurations.
- Amazon Agent: Installed on EC2 instances to gather data.
- Security Assessment Service: Analyses data and provides findings.
To use Amazon Inspector, configure the options, run the service, and it will generate a list of potential security issues. These findings are displayed in the Amazon Inspector console with detailed descriptions and recommendations for remediation. You can also retrieve findings through an API.
28.0.4 Amazon GuardDuty
Amazon GuardDuty is a threat detection service that continuously analyses metadata from your account and network activity. It utilises AWS CloudTrail events, Amazon VPC Flow Logs, and DNS logs. GuardDuty uses integrated threat intelligence, anomaly detection, and machine learning to identify threats accurately. It runs independently from your other AWS services, ensuring that it does not affect their performance or availability.
28.0.5 AWS Key Management Service (AWS KMS)
AWS Key Management Service (KMS) enables you to perform encryption operations using cryptographic keys, which are random strings of digits used for encrypting and decrypting data. AWS KMS allows you to create, manage, and use cryptographic keys and control their use across various services and applications. You can specify which IAM users and roles can manage keys and even temporarily disable keys to prevent their use. Your keys never leave AWS KMS, ensuring you maintain control.
28.0.6 AWS Web Application Firewall (WAF)
AWS WAF is a web application firewall that monitors network requests to your web applications. It works with Amazon CloudFront and an Application Load Balancer to block or allow traffic using a web access control list (ACL).
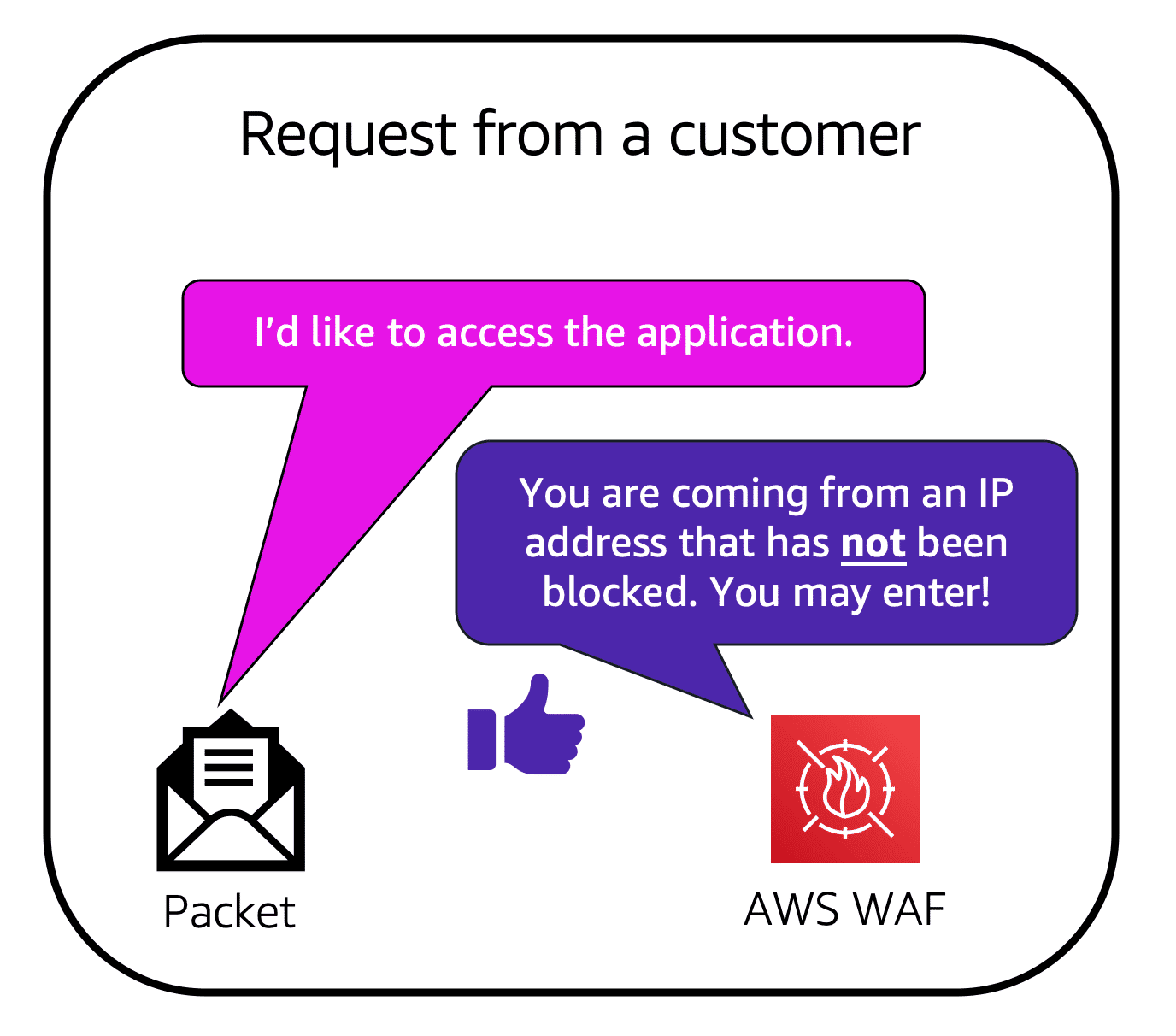
28.0.7 Example of AWS WAF in Action
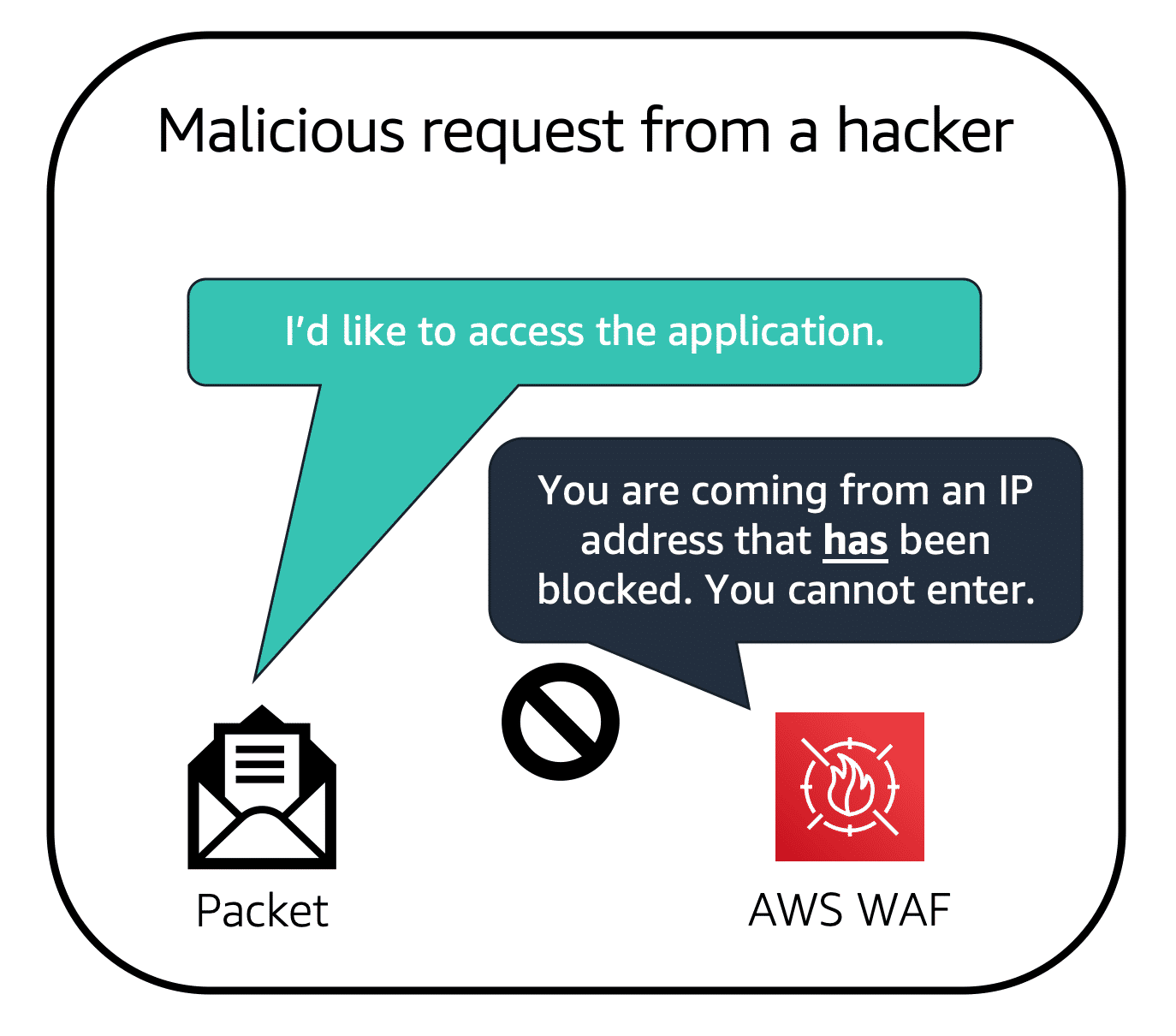
Suppose your application is receiving malicious network requests from several IP addresses. You want to prevent these requests but allow legitimate users to access your application. You configure the web ACL to allow all requests except those from the specified IP addresses. When a request comes into AWS WAF, it checks against the rules in the web ACL. If the request does not come from a blocked IP address, it allows access to the application.

Source: AWS Cloud Practitioner Essentials
If a request comes from one of the blocked IP addresses specified in the web ACL, AWS WAF denies access.
28.0.8 Conclusion
AWS offers a robust set of security services to help protect your applications and data. From encryption and automated security assessments with Amazon Inspector to intelligent threat detection with Amazon GuardDuty, AWS provides tools to enhance your security posture. Understanding and utilising these services ensures that your applications are secure, compliant, and resilient against various threats.